Difference between revisions of "PFSense and OPNsense"
m (→Using pfBlockerNG) |
m (→Troubleshooting) |
||
| (One intermediate revision by one user not shown) | |||
| Line 90: | Line 90: | ||
Per HOST or Per USER note: pfBlockerNG is not the best way to providing filtering while exempting specific hosts on the network. Although possible, it is problematic and difficult to configure. | Per HOST or Per USER note: pfBlockerNG is not the best way to providing filtering while exempting specific hosts on the network. Although possible, it is problematic and difficult to configure. | ||
| + | |||
| + | == Troubleshooting == | ||
| + | === The following CA/Certificate entries are expiring === | ||
| + | Beginning with 2.5.0 pfSense also allows you to renew the certificate in the web GUI in System > Certificate Manager > Certificates. | ||
| + | * Certificates are managed from System > Cert Manager, on the Certificates tab | ||
| + | |||
| + | Using pfSense as a Certificate Authority for your network: For network Chain of Trust. | ||
| + | |||
| + | === Force a DHCP lease to expire without impacting all other client leases === | ||
| + | |||
| + | If you give a static lease assignment after a client already has a dynamic lease, and you wish to trigger that client workstation or device to stop using the old dynamic IP from the previous lease and start using the new IP that was static mapped for it, without having physical access to the client device... here is what you do: | ||
| + | # In the GUI, go to Diagnostics/Edit File and load /var/dhcpd/var/db/dhcpd.leases~ | ||
| + | # Do the same for /var/dhcpd/var/db/dhcpd.leases | ||
| + | # goto Services -> DHCP Server and RESTART the DHCP server service. | ||
== Related == | == Related == | ||
Latest revision as of 23:58, 3 February 2024
OPNsense is a fork of PFSense. They are both nearly identical. If you consider the differences in the interfaces of the two, there is no more deviation than that of one version to the next of the same package.
OPNsense might be an excellent product, however, beyond installation there is absolutely no documentation on usage provided by the developers. It is a product without a manual. Unless you have a good background in networking concepts, firewalls, and pf (packet filter) under FreeBSD then you will likely struggle to do much beyond getting it up and running less any useful configuration.
With either PFSense or OPNsense you will be able to accomplish the same things. PFSense tends to be much better documented, however with that being said, neither are well documented. Please feel free to contribute what you have learned and use with these products here.
OPNSense Documentation
Contents
blocking websites
(1) DNSBL via dns:
If the built in DNS Forwarder or DNS Resolver are in use, an override can be configured which will resolve the website to block to an invalid IP address.
(2) via firewall rule:
This is not a feasible solution for sites that return low TTLs and spread the load across many servers.
A hostname may be entered in a network alias, and then that alias may be applied to a block rule.
Another option is finding all of a site's IP blocks, creating an alias with those networks, and blocking traffic to those destinations.
* Note: You have just blocked a web address or IP address and you notice a network client still has access. There is probably an active state established in the state pool and therefore the client continues to use a blocked site. In pfSense versioin 21.0.x goto DIAGNOSTICS -> STATES and either remove the specific active state or "Reset States" which will reset all client connections on the lan.
BLOCKING DIRECTION
Consider that your machine are attempting to contact external sites as well as external hosts are trying to contact machines on your network.
(1) Stop machines from attempting to contact hosts on your network
Create rules that block connections via your WAN.
- Firewall → Rules → WAN tab and press the upper-right + button
- for Action, select Block
- check the "Quick" box which will cause the rule to take action immediately on match.
- for Interface, select WAN
- for TCP/IP Version, select IPv4
- for Protocol, select any
- for Source: (Type: Single host or alias) and (Address: enter name of the URL alias which contains the IP addresses you want to block)
- for Destination select any
- enter a Description
- Save and Apply Changes
(2) Stop hosts on your network from contacting blacklisted external hosts
To prevent hosts on your network from communicating with blacklisted hosts online you create rules that block outgoing connections from your LAN. For each alias URL and each LAN just create a new firewall rule.
- Firewall → Rules → LAN tab and press the upper-right + button
- for Action, select Reject
- check the "Quick" box which will cause the rule to take action immediately on match.
- for Interface, select LAN
- for TCP/IP Version, select IPv4
- for Protocol, select any
- for Source select any
- for Destination: (Type: select Single host or alias) and (Address: enter the name of the URL alias which contains the IP addresses you want to block)
- enter a Description
- Save and Apply Changes
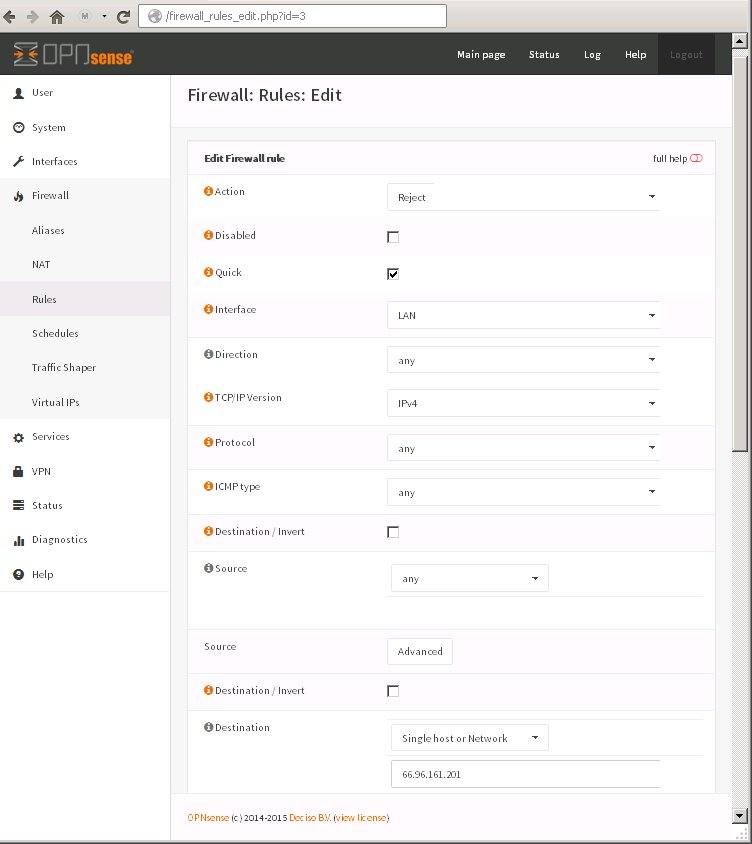
Example: Block all LAN workstations from being able to access the single IP address: 66.96.161.201 which will prevent users from being able to access a particular web site as well as any other traffic outgoing to that host.
Illustration shows using OPNsense to create a RULE under the tab FLOATING. This rule once created will be visible under the LAN tab. This rule is a REJECT rule. This is a host based blocking example that does _not_ use DNS blocking.
It is also possible to block a single workstation on your LAN, or even group of workstations from accessing a single host or group of hosts online. When creating the firewall rule such as the one used in the illustration above, if you specify a "Single Host or Network" for "Source" you will block access to the one workstation on your LAN. By defining an alias you can create a group of workstation also.
using aliases
Aliases can be defined for use with different blocking methods. In the single illustrated example above, an alias could be used to replace either the source or destination IP address. An alias can be used to define a host which may have multiple associated IP addressses like a group of workstations or an Internet destination where a DNS may resolve to more than one host. An alias could also be used to create a list of hosts which are unrelated other than you wish for them to be blocked. If a rule were added for each host to block individually, the rules list would grow quite large. By adding all of these hosts to an alias, only one firewall rule is necessary.
In one list it seems to partially fail if there are multiple hosts and some are IP and some are DNS.
URL aliases misunderstood
When you select Firewall → Aliases → URLs you will see the aliases with one or more URLs defined in the list. These are _NOT_ the specific URL of a web site you wish to block. This is not how it works. The URL is actually a resource. You enter the URL which is a file containing a list of hosts you wish to block.
- The URL is a link to a file containing many hosts you wish to block.
- The URL is not the address you wish to block.
Using pfBlockerNG
Differences between IPBL and DNSBL with the pfBlockerNG plugin
- DNSBL uses Unbound (DNS Resolver) to block network clients from accessing specified domains
- IPBL creates firewall rules to block network clients from accessing IPs and to keep those IPs from accessing the network.
DSNBL only has Unbound or Disabled, IPBL has a variety of actions, Denying inbound, outbound, both or simply matching and logging the traffic. IPBL has as many modes of enforcement of a firewall rule because it uses firewall rules to block traffic, where DNSBL simply uses the DNS resolver to send the client a different answer.
Per HOST or Per USER note: pfBlockerNG is not the best way to providing filtering while exempting specific hosts on the network. Although possible, it is problematic and difficult to configure.
Troubleshooting
The following CA/Certificate entries are expiring
Beginning with 2.5.0 pfSense also allows you to renew the certificate in the web GUI in System > Certificate Manager > Certificates.
- Certificates are managed from System > Cert Manager, on the Certificates tab
Using pfSense as a Certificate Authority for your network: For network Chain of Trust.
Force a DHCP lease to expire without impacting all other client leases
If you give a static lease assignment after a client already has a dynamic lease, and you wish to trigger that client workstation or device to stop using the old dynamic IP from the previous lease and start using the new IP that was static mapped for it, without having physical access to the client device... here is what you do:
- In the GUI, go to Diagnostics/Edit File and load /var/dhcpd/var/db/dhcpd.leases~
- Do the same for /var/dhcpd/var/db/dhcpd.leases
- goto Services -> DHCP Server and RESTART the DHCP server service.