Difference between revisions of "Simple Network Management Protocol"
m |
m (Reverted edits by Atekysepiko (Talk); changed back to last version by Admin) |
||
| (20 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
Used for monitoring network devices and encompassing a set of standard protocols. SNMP data contains information describing the network device configuration, and variables describing the state of the device. SNMP can be used to both read and write to the network device, such as reading the configuration and then modifying the configuration. SNMP is most commonly used for monitoring. | Used for monitoring network devices and encompassing a set of standard protocols. SNMP data contains information describing the network device configuration, and variables describing the state of the device. SNMP can be used to both read and write to the network device, such as reading the configuration and then modifying the configuration. SNMP is most commonly used for monitoring. | ||
| + | |||
| + | SNMP works by sending messages, called protocol data units (PDUs), to different parts of a network. SNMP-compliant devices, called agents, store data about themselves in Management Information Bases (MIBs) and return this data to the SNMP requesters. SNMP uses five basic messages (GET, GET-NEXT, GET-RESPONSE, SET, and TRAP) to communicate between the SNMP manager and the SNMP agent. There are variations to account for additional message types (see the six listed below) based on the version of SNMP being used. Many network elements support only SNMPv1 and SNMPv2c. Support for SNMPv3 is minimal. | ||
Information from network devices may be retrieved via | Information from network devices may be retrieved via | ||
| Line 8: | Line 10: | ||
*TRAP | *TRAP | ||
*INFORM | *INFORM | ||
| − | Data may be written using | + | Data may be written using |
*SET | *SET | ||
| − | Variables accessed by SNMP are organized in hierarchies. These hierarchies, and other metadata, are described by Management Information Bases (MIBs). | + | description |
| + | |||
| + | :*The read command is used by an NMS to monitor managed devices. The NMS examines different variables that are maintained by managed devices. | ||
| + | :*The write command is used by an NMS to control managed devices. The NMS changes the values of variables stored within managed devices. | ||
| + | :*The trap command is used by managed devices to asynchronously report events to the NMS. When certain types of events occur, a managed device sends a trap to the NMS. | ||
| + | |||
| + | <big>SNMP uses the default '''UDP port 161''' for general SNMP messages and '''UDP port 162''' for SNMP trap messages.</big> SNMP uses an unsupervised or connectionless communication link. | ||
| + | |||
| + | The GET and GET-NEXT messages allow the manager to request information for a specific variable. The agent, upon receiving a GET or GET-NEXT message, will issue a GET-RESPONSE message to the SNMP manager with either the information requested or an error indication as to why the request cannot be processed. A SET message allows the SNMP manager to request a change be made to the value of a specific variable in the case of an alarm remote that will operate a relay. The SNMP agent will then respond with a GET-RESPONSE message indicating the change has been made or an error indication as to why the change cannot be made. The SNMP TRAP message allows the agent to spontaneously inform the SNMP manager of an "important" event. | ||
| + | |||
| + | (GET, GET-NEXT, and SET) are only issued by the SNMP manager. The TRAP message is the only message capable of being initiated by an SNMP agent, it is the message used by DPS Remote Telemetry Units (RTUs) to report alarms. This notifies the SNMP manager as soon as an alarm condition occurs, instead of waiting for the SNMP manager to ask. | ||
| + | |||
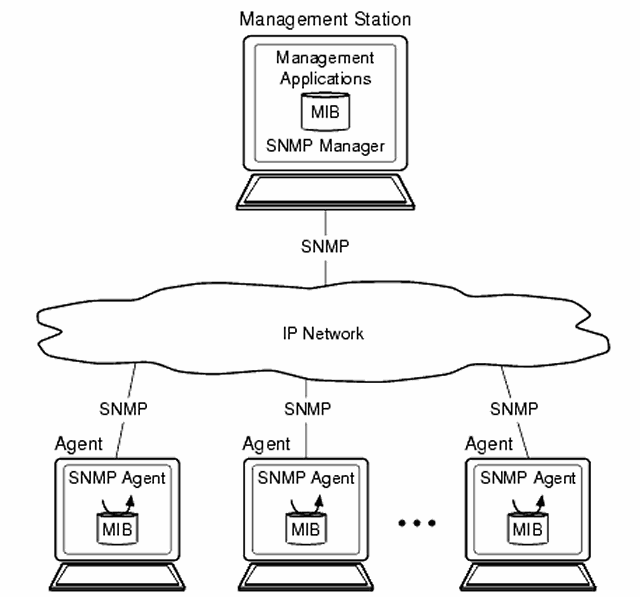
| + | [[Image:snmpipnetwork.png]] | ||
| + | |||
| + | Simple Network Management Protocol (SNMP) is a widely used protocol for monitoring the health and welfare of network equipment (eg. routers), computer equipment and even devices like UPSs. Two versions of SNMP exist: SNMP version 1 (SNMPv1) and SNMP version 2 (SNMPv2). Both versions have a number of features in common, but SNMPv2 offers enhancements, such as additional protocol operations. Standardization of yet another version of SNMP—SNMP Version 3 (SNMPv3)—is pending. | ||
| + | |||
| + | Variables accessed by SNMP are organized in hierarchies. These hierarchies, and other metadata, are described by Management Information Bases (MIBs). An SNMP-managed network consists of three key components: managed devices, agents, and network-management systems (NMSs). | ||
| + | |||
| + | SNMP must account for and adjust to incompatibilities between managed devices. Different computers use different data representation techniques, which can compromise the capability of SNMP to exchange information between managed devices. SNMP uses a subset of Abstract Syntax Notation One to accommodate communication between diverse systems. | ||
| + | |||
| + | === versions === | ||
| + | |||
| + | SNMPv1 SNMPv1, which implements community-based security | ||
| + | SNMPv2c SNMPv2 with community-based security | ||
| + | SNMPv2u SNMPv2 with user-based security | ||
| + | SNMPv2 SNMPv2 with party-based security | ||
| + | SNMPv3 SNMPv3, which implements user-based security | ||
| + | |||
| + | === SNMP Messages === | ||
| + | |||
| + | SNMP messages may be initiated by either the network management system (NMS) or by the network element. | ||
| + | |||
| + | An SNMP TRAP is a message which is initiated by a network element and sent to the network management system. For example, a router could send a message if one of it's redundant power supplies fails or a printer could send an SNMP trap when it is out of paper. | ||
| + | |||
| + | An SNMP GET is a message which is initiated by the network management system when it wants to retrieve some data from a network element. For example, the network management system might query a router for the utilization on a WAN link every 5 minutes. It could then create charts and graphs from that data, or it could warn the operator when the link was overutilized. | ||
| + | |||
| + | An SNMP SET is a message which is initiated by the NMS when it wants to change data on a network element. For example, the NMS may wish to alter a static route on a router. | ||
| + | |||
| + | === The SNMP MIB === | ||
| + | |||
| + | The SNMP MIB, or Management Information Base, is a collection of variables which is shared between the NMS and the network element (NE). | ||
| + | |||
| + | The MIB is extensible, which means that hardware and software manufacturers can add new variables to the MIB. These new MIB definitions must be added both to the network element and to the network management system. | ||
| + | |||
| + | === SNMP Community Strings === | ||
| + | |||
| + | The most basic form of SNMP security is the Community String. | ||
| + | |||
| + | SNMP Community Strings are like passwords for network elements. | ||
| + | |||
| + | Most often, there is one community string which is used for read-only access to a network element. The default value for this community string is often "public". Using this community string like a password, the NMS can retrieve data from network elements. | ||
| + | |||
| + | Less often, there is also a read-write community string. The default value for this is often "private". Using this community string, the NMS can actually change MIB variables on a network element. | ||
| + | |||
| + | === Communication Architecture === | ||
| + | |||
| + | To get information from an SNMP device, a "manager" (SNMP terminology for a client) will send a "GetRequest" or "GetNextRequest" to an "agent" (the SNMP term for a server) and the requested information or an error message will be sent back in a "Response." If a manager wants to modify information on an agent, a "SetRequest" will be sent with a corresponding response to confirm or report an error. | ||
| + | |||
| + | The unsolicited message form is called a "trap." This kind of message is usually sent by agents on start-up, on status change and in response to error conditions. Traps are not only unsolicited but they are also unreliable. Like syslog messages they are sent via User Datagram Protocol and whether they are received depends on whether they make it to the destination (remember, UDP is an unreliable, best-effort service) and whether the manager is listening. | ||
| + | |||
| + | The information on the agent is stored in what is called a Management Information Base (MIB). This is a hierarchical data structure (not, as it is often mistakenly called, a database) that describes all the "objects" that a device can report the status of and, in some cases, set the value of. | ||
| + | |||
| + | === Direct Router and Server monitoring with SNMP === | ||
| + | |||
| + | SNMP provides a method of managing network hosts such as workstation or server computers, routers, bridges, and hubs from a centrally-located computer running network management software. SNMP performs management services by using a distributed architecture of management systems and agents | ||
| + | |||
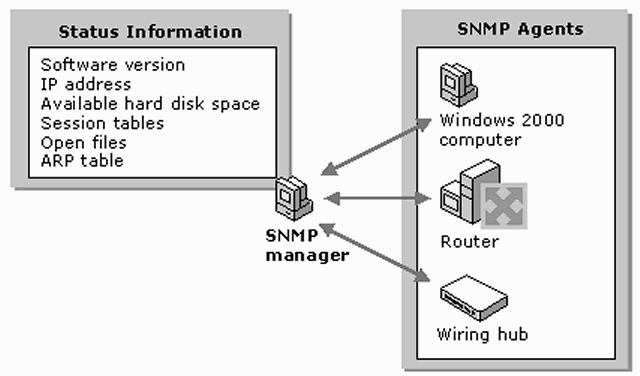
| + | [[Image:snmpipnetwork2.png]] | ||
| + | |||
| + | The monitored device(s) must be equipped with SNMP, SNMP must be enabled on the device and the machine PRTG must be allowed access to the SNMP interface. The most common usage is monitoring the bandwidth usage of leased lines, routers and firewalls. But you can also monitor the usage of servers, managed switches or printers. | ||
| + | |||
| + | === Monitoring Microsoft Windows === | ||
| + | |||
| + | In order to monitor Windows Servers/Workstations the SNMP Service has to be started, if this isn't the case you have to install it. | ||
| + | |||
| + | # Open the Windows Components wizard | ||
| + | # In Components, click Management and Monitoring Tools (but do not select or clear its check box), and then click Details. | ||
| + | # Select Simple Network Management Protocol check box, and click OK. | ||
| + | # Click Next. | ||
| + | |||
| + | To open the Windows Components wizard, click Start, point to Settings, click Control Panel, double-click Add/Remove Programs, and then click Add/Remove Windows Components. | ||
| + | |||
| + | Certain Windows components require configuration before thay can be used. If you installed one or more of these components, but did not configure them, when you click Add/Remove Windows Components, a list of components that need to be configured is displayed. To start the Windows Components wizard, click Components. | ||
| + | |||
| + | You must be logged on as an administrator or a member of the Administrators group in order to complete this procedure. If your computer is connected to a network, network policy settings might also prevent you from completing this procedure. | ||
| + | |||
| + | SNMP starts automatically after installation. For your monitoring software set the Sample-Rate at least to 10 seconds. | ||
| + | |||
| + | === Security of SNMP and Exploitation === | ||
| + | |||
| + | SNMP is vulnerable because it is often automatically installed on many network devices with "public" as the read string and "private" as the write string. This would mean that systems might be installed on a network without any knowledge that SNMP is functioning and using these default keys. | ||
| + | |||
| + | This default installation of SNMP provides an attacker with the means to perform reconnaissance on a system, and, an exploit that can be used to create a denial of service. SNMP MIBs provide information such as the system name, location, contacts, and sometimes even phone numbers. This soft intelligence can be very useful in social engineering. An attacker could call an organization and use the system contact and system name to gain a password from an unsuspecting user. The telephone number for the system contact could be used to provide a dialing prefix that the attacker could use for war dialing. | ||
| + | |||
| + | SNMP information also provides a great deal of hard intelligence about the system. One MIB provides the system description that reveals the operating system that the host is using. This can be matched against known exploits that would allow the attacker to gain further access into the SNMP host. SNMP data also provides interface descriptions, types, and other interface configuration information. This interface information can be gathered from more that one system to allow an attacker to piece together a network map of an organization showing how systems are interconnected. Some MIBs are writeable allowing the attacker to change the system configuration creating a denial of service opportunity. One such MIB is "ifAdminStatus". "IfAdminStatus" is set to "1" when the interface is operational and to "2" when it is down. An attacker could set "ifAdminStatus" to "2" using the SNMP set PDU which could disconnect the host from the network creating a denial service. | ||
| + | |||
| + | "Public" and "private" are not the only default or easy guessable community stings which are used. Some Solaris systems use "all private" by default. HP SNMP agents have been known to use "snmpd" as their default community strings. A Compaq customer advisory notice stated that, "Insight Manager Console using Compaq Insight Manager Version 3.00" will only use the first three characters of any community string that is used, making this agent very susceptible to a brute force SNMP attack. | ||
| + | |||
| + | To harden your security exercise conservative use of SNMP. SNMP should not be enabled on devices that do not require it. It is better to push the information from the managed devices using SNMP traps rather that polling the devices using SNMP agents. SNMP community write strings can be disable if the network management platform only poll devices and does not change the remote devices configuration. | ||
| + | |||
| + | If SNMP is needed the community strings should be set at their maximum length and include a combination of letters, numbers, and special characters to avoid a brute force attack. All network devices should be scanned using an SNMP vulnerability scanner to ensure that they do not use the default community strings. | ||
| + | |||
| + | SNMP access should also be limited to only the devices that require SNMP for monitoring. This can be accomplished by allowing only authorized clients to access UDP port 161. All access to UDP port 161 should be denied from external networks. | ||
| | ||
Latest revision as of 11:50, 24 November 2010
Used for monitoring network devices and encompassing a set of standard protocols. SNMP data contains information describing the network device configuration, and variables describing the state of the device. SNMP can be used to both read and write to the network device, such as reading the configuration and then modifying the configuration. SNMP is most commonly used for monitoring.
SNMP works by sending messages, called protocol data units (PDUs), to different parts of a network. SNMP-compliant devices, called agents, store data about themselves in Management Information Bases (MIBs) and return this data to the SNMP requesters. SNMP uses five basic messages (GET, GET-NEXT, GET-RESPONSE, SET, and TRAP) to communicate between the SNMP manager and the SNMP agent. There are variations to account for additional message types (see the six listed below) based on the version of SNMP being used. Many network elements support only SNMPv1 and SNMPv2c. Support for SNMPv3 is minimal.
Information from network devices may be retrieved via
- GET
- GETNEXT
- GETBULK
Data may be streamed using
- TRAP
- INFORM
Data may be written using
- SET
description
- The read command is used by an NMS to monitor managed devices. The NMS examines different variables that are maintained by managed devices.
- The write command is used by an NMS to control managed devices. The NMS changes the values of variables stored within managed devices.
- The trap command is used by managed devices to asynchronously report events to the NMS. When certain types of events occur, a managed device sends a trap to the NMS.
SNMP uses the default UDP port 161 for general SNMP messages and UDP port 162 for SNMP trap messages. SNMP uses an unsupervised or connectionless communication link.
The GET and GET-NEXT messages allow the manager to request information for a specific variable. The agent, upon receiving a GET or GET-NEXT message, will issue a GET-RESPONSE message to the SNMP manager with either the information requested or an error indication as to why the request cannot be processed. A SET message allows the SNMP manager to request a change be made to the value of a specific variable in the case of an alarm remote that will operate a relay. The SNMP agent will then respond with a GET-RESPONSE message indicating the change has been made or an error indication as to why the change cannot be made. The SNMP TRAP message allows the agent to spontaneously inform the SNMP manager of an "important" event.
(GET, GET-NEXT, and SET) are only issued by the SNMP manager. The TRAP message is the only message capable of being initiated by an SNMP agent, it is the message used by DPS Remote Telemetry Units (RTUs) to report alarms. This notifies the SNMP manager as soon as an alarm condition occurs, instead of waiting for the SNMP manager to ask.
Simple Network Management Protocol (SNMP) is a widely used protocol for monitoring the health and welfare of network equipment (eg. routers), computer equipment and even devices like UPSs. Two versions of SNMP exist: SNMP version 1 (SNMPv1) and SNMP version 2 (SNMPv2). Both versions have a number of features in common, but SNMPv2 offers enhancements, such as additional protocol operations. Standardization of yet another version of SNMP—SNMP Version 3 (SNMPv3)—is pending.
Variables accessed by SNMP are organized in hierarchies. These hierarchies, and other metadata, are described by Management Information Bases (MIBs). An SNMP-managed network consists of three key components: managed devices, agents, and network-management systems (NMSs).
SNMP must account for and adjust to incompatibilities between managed devices. Different computers use different data representation techniques, which can compromise the capability of SNMP to exchange information between managed devices. SNMP uses a subset of Abstract Syntax Notation One to accommodate communication between diverse systems.
Contents
versions
SNMPv1 SNMPv1, which implements community-based security SNMPv2c SNMPv2 with community-based security SNMPv2u SNMPv2 with user-based security SNMPv2 SNMPv2 with party-based security SNMPv3 SNMPv3, which implements user-based security
SNMP Messages
SNMP messages may be initiated by either the network management system (NMS) or by the network element.
An SNMP TRAP is a message which is initiated by a network element and sent to the network management system. For example, a router could send a message if one of it's redundant power supplies fails or a printer could send an SNMP trap when it is out of paper.
An SNMP GET is a message which is initiated by the network management system when it wants to retrieve some data from a network element. For example, the network management system might query a router for the utilization on a WAN link every 5 minutes. It could then create charts and graphs from that data, or it could warn the operator when the link was overutilized.
An SNMP SET is a message which is initiated by the NMS when it wants to change data on a network element. For example, the NMS may wish to alter a static route on a router.
The SNMP MIB
The SNMP MIB, or Management Information Base, is a collection of variables which is shared between the NMS and the network element (NE).
The MIB is extensible, which means that hardware and software manufacturers can add new variables to the MIB. These new MIB definitions must be added both to the network element and to the network management system.
SNMP Community Strings
The most basic form of SNMP security is the Community String.
SNMP Community Strings are like passwords for network elements.
Most often, there is one community string which is used for read-only access to a network element. The default value for this community string is often "public". Using this community string like a password, the NMS can retrieve data from network elements.
Less often, there is also a read-write community string. The default value for this is often "private". Using this community string, the NMS can actually change MIB variables on a network element.
Communication Architecture
To get information from an SNMP device, a "manager" (SNMP terminology for a client) will send a "GetRequest" or "GetNextRequest" to an "agent" (the SNMP term for a server) and the requested information or an error message will be sent back in a "Response." If a manager wants to modify information on an agent, a "SetRequest" will be sent with a corresponding response to confirm or report an error.
The unsolicited message form is called a "trap." This kind of message is usually sent by agents on start-up, on status change and in response to error conditions. Traps are not only unsolicited but they are also unreliable. Like syslog messages they are sent via User Datagram Protocol and whether they are received depends on whether they make it to the destination (remember, UDP is an unreliable, best-effort service) and whether the manager is listening.
The information on the agent is stored in what is called a Management Information Base (MIB). This is a hierarchical data structure (not, as it is often mistakenly called, a database) that describes all the "objects" that a device can report the status of and, in some cases, set the value of.
Direct Router and Server monitoring with SNMP
SNMP provides a method of managing network hosts such as workstation or server computers, routers, bridges, and hubs from a centrally-located computer running network management software. SNMP performs management services by using a distributed architecture of management systems and agents
The monitored device(s) must be equipped with SNMP, SNMP must be enabled on the device and the machine PRTG must be allowed access to the SNMP interface. The most common usage is monitoring the bandwidth usage of leased lines, routers and firewalls. But you can also monitor the usage of servers, managed switches or printers.
Monitoring Microsoft Windows
In order to monitor Windows Servers/Workstations the SNMP Service has to be started, if this isn't the case you have to install it.
- Open the Windows Components wizard
- In Components, click Management and Monitoring Tools (but do not select or clear its check box), and then click Details.
- Select Simple Network Management Protocol check box, and click OK.
- Click Next.
To open the Windows Components wizard, click Start, point to Settings, click Control Panel, double-click Add/Remove Programs, and then click Add/Remove Windows Components.
Certain Windows components require configuration before thay can be used. If you installed one or more of these components, but did not configure them, when you click Add/Remove Windows Components, a list of components that need to be configured is displayed. To start the Windows Components wizard, click Components.
You must be logged on as an administrator or a member of the Administrators group in order to complete this procedure. If your computer is connected to a network, network policy settings might also prevent you from completing this procedure.
SNMP starts automatically after installation. For your monitoring software set the Sample-Rate at least to 10 seconds.
Security of SNMP and Exploitation
SNMP is vulnerable because it is often automatically installed on many network devices with "public" as the read string and "private" as the write string. This would mean that systems might be installed on a network without any knowledge that SNMP is functioning and using these default keys.
This default installation of SNMP provides an attacker with the means to perform reconnaissance on a system, and, an exploit that can be used to create a denial of service. SNMP MIBs provide information such as the system name, location, contacts, and sometimes even phone numbers. This soft intelligence can be very useful in social engineering. An attacker could call an organization and use the system contact and system name to gain a password from an unsuspecting user. The telephone number for the system contact could be used to provide a dialing prefix that the attacker could use for war dialing.
SNMP information also provides a great deal of hard intelligence about the system. One MIB provides the system description that reveals the operating system that the host is using. This can be matched against known exploits that would allow the attacker to gain further access into the SNMP host. SNMP data also provides interface descriptions, types, and other interface configuration information. This interface information can be gathered from more that one system to allow an attacker to piece together a network map of an organization showing how systems are interconnected. Some MIBs are writeable allowing the attacker to change the system configuration creating a denial of service opportunity. One such MIB is "ifAdminStatus". "IfAdminStatus" is set to "1" when the interface is operational and to "2" when it is down. An attacker could set "ifAdminStatus" to "2" using the SNMP set PDU which could disconnect the host from the network creating a denial service.
"Public" and "private" are not the only default or easy guessable community stings which are used. Some Solaris systems use "all private" by default. HP SNMP agents have been known to use "snmpd" as their default community strings. A Compaq customer advisory notice stated that, "Insight Manager Console using Compaq Insight Manager Version 3.00" will only use the first three characters of any community string that is used, making this agent very susceptible to a brute force SNMP attack.
To harden your security exercise conservative use of SNMP. SNMP should not be enabled on devices that do not require it. It is better to push the information from the managed devices using SNMP traps rather that polling the devices using SNMP agents. SNMP community write strings can be disable if the network management platform only poll devices and does not change the remote devices configuration.
If SNMP is needed the community strings should be set at their maximum length and include a combination of letters, numbers, and special characters to avoid a brute force attack. All network devices should be scanned using an SNMP vulnerability scanner to ensure that they do not use the default community strings.
SNMP access should also be limited to only the devices that require SNMP for monitoring. This can be accomplished by allowing only authorized clients to access UDP port 161. All access to UDP port 161 should be denied from external networks.