Difference between revisions of "SAM Hive Encryption"
(→Recovery) |
|||
| (8 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| − | Most commonly associated with "This is Microsoft Support" telephone scam. | + | Most commonly associated with "This is Microsoft Support" telephone scam or The [[Microsoft Tech Support Phone Scam]]. |
[[File:syskey.png]] | [[File:syskey.png]] | ||
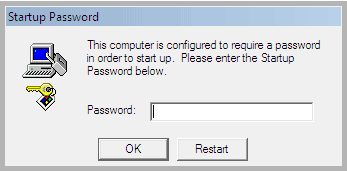
There is a feature built into Windows that can be used to add encryption to the SAM hive of the Windows registry. It is a legitimate feature of Microsoft Windows. However, it is now being used as part of a Ransom Scam where the caller poses as an employee of Microsoft reaching out to help you resolve some kind of security threat to your computer. Via remote access the caller, once permitted, enables in windows policy SAM hive encryption. Then the caller announces that you must pay money to regain access to your computer. | There is a feature built into Windows that can be used to add encryption to the SAM hive of the Windows registry. It is a legitimate feature of Microsoft Windows. However, it is now being used as part of a Ransom Scam where the caller poses as an employee of Microsoft reaching out to help you resolve some kind of security threat to your computer. Via remote access the caller, once permitted, enables in windows policy SAM hive encryption. Then the caller announces that you must pay money to regain access to your computer. | ||
| + | |||
| + | == SysKey Utility == | ||
| + | The Microsoft Windows 2000, Microsoft Windows XP, and Microsoft Windows 2003 Security Accounts Management Database (SAM) stores hashed copies of user passwords. This database is encrypted with a locally stored system key. To keep the SAM database secure, Windows requires that the password hashes are encrypted. Windows prevents the use of stored, unencrypted password hashes. | ||
| + | |||
| + | You can use the SysKey utility to secure the Windows Security Accounts Manager database. The SysKey utility can be used to configure a start-up password that must be entered to decrypt the system key so that Windows can access the SAM database. | ||
| + | |||
| + | To Configure Windows System Key Protection, follow these steps: | ||
| + | |||
| + | #At a command prompt, type syskey, and then press ENTER. | ||
| + | #In the Securing the Windows Account Database dialog box, note that the Encryption Enabled option is selected and is the only option available. When this option is selected, Windows will always encrypt the SAM database. | ||
| + | #Click Update. | ||
| + | #Click Password Startup if you want to require a password to start Windows. Use a complex password that contains a combination of upper case and lower case letters, numbers, and symbols. The startup password must be at least 12 characters long and can be up to 128 characters long. Note If you must remotely restart a computer that requires a password (if you use the Password Startup option), a person must be at the local console during the restart. Use this option only if a trusted security administrator will be available to type the Startup password. | ||
| + | #Click System Generated Password if you do not want to require a startup password. | ||
| + | #Select either of the following options: Click Store Startup Key on Floppy Disk to store the system startup password on a floppy disk. This requires that someone insert the floppy disk to start the operating system. Click Store Startup Key Locally to store the encryption key on the hard disk of the local computer. This is the default option. | ||
| + | #Click OK two times to complete the procedure. | ||
| + | |||
| + | Remove the SAM encryption key from the local hard disk by using the Store Startup Key on Floppy Disk option for optimum security. This provides the highest level of protection for the SAM database. | ||
| + | |||
| + | Always create a back-up floppy disk if you use the Store Startup Key on Floppy Disk option. You can restart the system remotely if someone is available to insert the floppy disk into the computer when it restarts. | ||
| + | |||
| + | See: Microsoft Support Article 310105 | ||
| + | |||
| + | == Malicious Use == | ||
| + | |||
| + | As with many of the [[Microsoft Tech Support Phone Scam]]s the goal of the scam artist is to intimidate you into paying money or something very bad will happen to your computer and data. One technique this can be accomplished is by enabling SAM hive encryption after you have been tricked into allowing the scammer remote access, or you have downloaded and installed malicious software. | ||
| + | |||
| + | == Recovery == | ||
| + | |||
| + | The scammers often prevent easy recovery by deleting all System Restore points on the machine, which normally house backup copies of the registry hives. If a restore point is available, it is the easiest means to recover the machine by restoring to a point prior to the hive being encrypted. | ||
| + | |||
| + | === Manually Restore Registry Hives === | ||
| + | |||
| + | This is verified to have worked on a system where the automatic backup of the registry was still intact. | ||
| + | |||
| + | #Boot from Hiren's boot or a live linux distro via USB or optical media | ||
| + | #Mount the Windows partition | ||
| + | #Navigate to %SYSTEMROOT%\system32\config | ||
| + | #copy the registry hives (these are the damaged ones) to another location or media | ||
| + | #Navigate to %SYSTEMROOT%\system32\config\RegBack | ||
| + | #copy all the backup registry hives in this folder and paste to the config folder overwriting the damaged registry hives | ||
| + | #Reboot | ||
| + | |||
| + | You may find that there are no backup registry hives in %SYSTEMROOT%\system32\config\RegBack because the intruder removed them. However, it has been my experience that they are still present. | ||
| + | |||
| + | == Resources == | ||
| + | |||
| + | * [https://fixedit.itxpress.biz/2015/01/16/unlocking-after-the-microsoft-support-phone-scam/ Unlocking After the Microsoft Support Phone Scam] | ||
| + | * [https://www.bleepingcomputer.com/forums/t/470753/remove-a-startup-password-before-account-screen/ BleepingComputer.com- Remove a startup password before account screen] | ||
| + | * [https://answers.microsoft.com/en-us/windows/forum/windows_7-security/windows-7-locked-after-scam-call-syskey/5933abb9-4f1b-46cf-bc6a-f81ed33c0a85?auth=1 Windows 7 Locked after scam call - SYSKEY] | ||
| | ||
Latest revision as of 19:35, 23 March 2017
Most commonly associated with "This is Microsoft Support" telephone scam or The Microsoft Tech Support Phone Scam.
There is a feature built into Windows that can be used to add encryption to the SAM hive of the Windows registry. It is a legitimate feature of Microsoft Windows. However, it is now being used as part of a Ransom Scam where the caller poses as an employee of Microsoft reaching out to help you resolve some kind of security threat to your computer. Via remote access the caller, once permitted, enables in windows policy SAM hive encryption. Then the caller announces that you must pay money to regain access to your computer.
Contents
SysKey Utility
The Microsoft Windows 2000, Microsoft Windows XP, and Microsoft Windows 2003 Security Accounts Management Database (SAM) stores hashed copies of user passwords. This database is encrypted with a locally stored system key. To keep the SAM database secure, Windows requires that the password hashes are encrypted. Windows prevents the use of stored, unencrypted password hashes.
You can use the SysKey utility to secure the Windows Security Accounts Manager database. The SysKey utility can be used to configure a start-up password that must be entered to decrypt the system key so that Windows can access the SAM database.
To Configure Windows System Key Protection, follow these steps:
- At a command prompt, type syskey, and then press ENTER.
- In the Securing the Windows Account Database dialog box, note that the Encryption Enabled option is selected and is the only option available. When this option is selected, Windows will always encrypt the SAM database.
- Click Update.
- Click Password Startup if you want to require a password to start Windows. Use a complex password that contains a combination of upper case and lower case letters, numbers, and symbols. The startup password must be at least 12 characters long and can be up to 128 characters long. Note If you must remotely restart a computer that requires a password (if you use the Password Startup option), a person must be at the local console during the restart. Use this option only if a trusted security administrator will be available to type the Startup password.
- Click System Generated Password if you do not want to require a startup password.
- Select either of the following options: Click Store Startup Key on Floppy Disk to store the system startup password on a floppy disk. This requires that someone insert the floppy disk to start the operating system. Click Store Startup Key Locally to store the encryption key on the hard disk of the local computer. This is the default option.
- Click OK two times to complete the procedure.
Remove the SAM encryption key from the local hard disk by using the Store Startup Key on Floppy Disk option for optimum security. This provides the highest level of protection for the SAM database.
Always create a back-up floppy disk if you use the Store Startup Key on Floppy Disk option. You can restart the system remotely if someone is available to insert the floppy disk into the computer when it restarts.
See: Microsoft Support Article 310105
Malicious Use
As with many of the Microsoft Tech Support Phone Scams the goal of the scam artist is to intimidate you into paying money or something very bad will happen to your computer and data. One technique this can be accomplished is by enabling SAM hive encryption after you have been tricked into allowing the scammer remote access, or you have downloaded and installed malicious software.
Recovery
The scammers often prevent easy recovery by deleting all System Restore points on the machine, which normally house backup copies of the registry hives. If a restore point is available, it is the easiest means to recover the machine by restoring to a point prior to the hive being encrypted.
Manually Restore Registry Hives
This is verified to have worked on a system where the automatic backup of the registry was still intact.
- Boot from Hiren's boot or a live linux distro via USB or optical media
- Mount the Windows partition
- Navigate to %SYSTEMROOT%\system32\config
- copy the registry hives (these are the damaged ones) to another location or media
- Navigate to %SYSTEMROOT%\system32\config\RegBack
- copy all the backup registry hives in this folder and paste to the config folder overwriting the damaged registry hives
- Reboot
You may find that there are no backup registry hives in %SYSTEMROOT%\system32\config\RegBack because the intruder removed them. However, it has been my experience that they are still present.
Resources
- Unlocking After the Microsoft Support Phone Scam
- BleepingComputer.com- Remove a startup password before account screen
- Windows 7 Locked after scam call - SYSKEY